words: 1453 (not counting references)
PREMISE
Using Internet of Things sensors to help indicate if there is trojan malware present in a mobile phone.
SYNOPSIS
Cybercrime victimisation can happen to all. It can happen without the victim even knowing it. And even then, were it to be discovered, the damage could already have been done. This is a prime example of trojan malware. A sneaky cyberattack that is known to hid extremely well to creep in of its victims. Therefore making it a difficult enemy to beat. This project aims to highlight this cybercrime issue and offers a way to help victims recognise these enemies, so that a swift counterattack can be made. With the help of IoT technology and experiments, this goal shall advance.
CONTEXT
In the age of digitalisation the ways of socialising, working and shopping have changed drastically. Especially since the start of the pandemic there has been a rapid increase in digital communication (Monteith, Bauer, Alda, Geddes, Whybrow, & Glenn, 2021). This brings good and bad side effects, with one of the bad ones being cybercrime. Cybercrime has skyrocketed with 600% due to the pandemic, mostly through mobile platforms (PurpleSec, 2021). These attacks were able to happen due to one of their greatest weapons: malware. Malware can be defined as a harmful piece of software that was written with the intent of doing harm, to people and their data and devices. Malware is continuously becoming more and more sophisticated, intelligent and versatile, making it difficult for people to see their red flags (Chng, Lu, Kumar, & Yau, 2022). On average, it takes people around 207 days to notice the hint of a breach (Sobers, 2021). Especially trojan malware, which makes up 51.45% of all malware, is a type of malware that disguises itself as a legitimate program, thus therefore can rarely be found (PurpleSec, 2021). One of the two most targeted victims are young adults, as their needs for diversion, entertainment and social relationships make them lacks in protecting themselves online (Kokolakis, 2017). The other regular victim is IoT.
Internet of Things
IoT, Internet of Things, is a system that is able to connect sensors with devices, such as a smart doorbell. These sensors are then able to “talk” to the cloud through connectivity. Once the data gets to the cloud the software processes it and is able to make it perform an action, for example ringing an alarm when the sensor detects movement (McClelland, 2016). Because of the constant connectivity to the Internet, and lack of security, IoT has become vulnerable to malware attacks (Valeo Networks, 2021). However, as the saying from Baltasar Gracián (2015) goes, “deal with people from whom you can learn.” Despite IoT downfalls, it also possesses benefits that could help the malware problem. Capability to provide: timely information, great response times, automation, insights created by high volumes of data, great communication and improved data quality, to name a few (Brous, Janssen, & Herder, 2020).
These benefits could perhaps be of assistants when thinking about the problem. Malware comes onto a phone in multiple ways, by infected applications, malvertising (clicking online ads with malware) and or scams or phishing (La Porta, 2021). When malware has infiltrated the phone, numerous unseen signs can be detected: overheated phone, drained battery, frequently pop-up ads, slow phone performance, unexplained apps, surge in data consumption, weird charges, expensive phone bills and overall strange spikes (Lishchuk, 2021). In view of the fact that malware is difficult to detect with human eyes, IoT and its sensors can perhaps come into play. A mobile phone has three main categories of sensors: motion, environment and position (Tillu, 2021). Each category consist of various sensors with its own purpose to help assist the user. Connecting the malware signs with these mobile sensors, it could feasibly help detect strange behaviour that could be linked to malware.
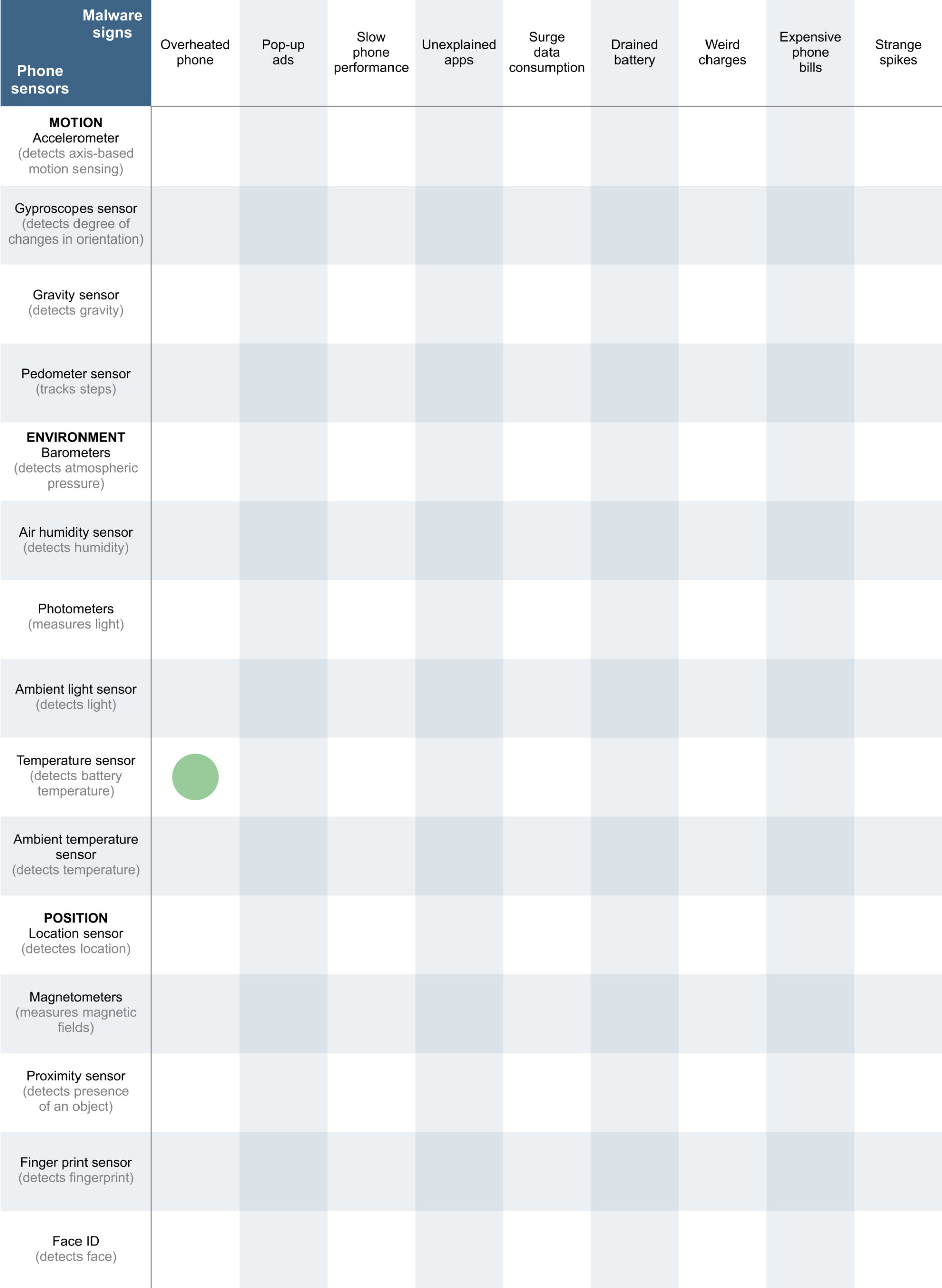
Results from the table show that not a lot of links can be made. However, the temperature sensor in the phone could collect data about an overheating phone. The name “temperature sensor” may sound misleading, but Chau (2019) tells that “Most of the smartphones are not equipped with air temperature sensors but they are all equipped with battery temperature sensors.” This temperature sensor can measure battery temperature, state and voltage (Zarkov, 2020).
PROJECT OVERVIEW
Now that there is a clear direction in this experiment, it is time to prototype. The scope of this research will primarily focus on implementation prototypes with a hint of look and feel (Houde, & Hill, 1997). Implementation prototypes focus on answering technical questions, wondering if certain elements could be made to work to achieve a certain goal. In this case, the success of the temperature sensor to detect malware will be tested, seeing if the idea is even plausible. Look and feel prototypes are build to explore the experience of an element, how would users look and want to interact with it. If malware were to be detected, then the user needs to be informed about this information in a fast and easy way.

ITERATION – 1
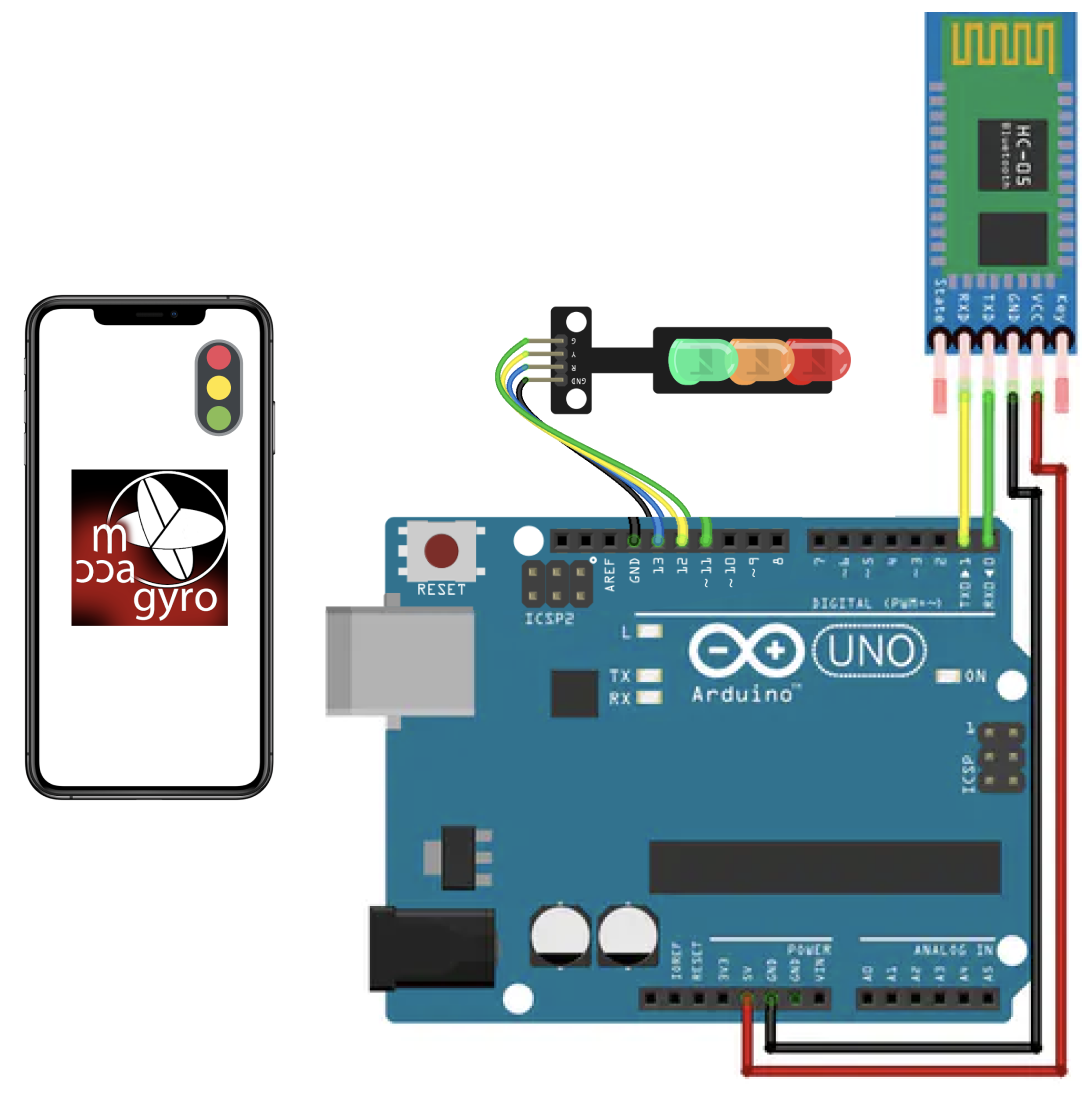
The aim of the first iteration was to make contact with the temperature sensor and to read its data. An old phone will be used for this experiment. To be able to read this sensor an application that measures it needs to be downloaded. Furthermore, this application also needs to be able to send the data to Arduino, an open-source prototyping platform, so it can be worked with. To send and receive data between Arduino and an Android, a bluetooth module is needed.
Using

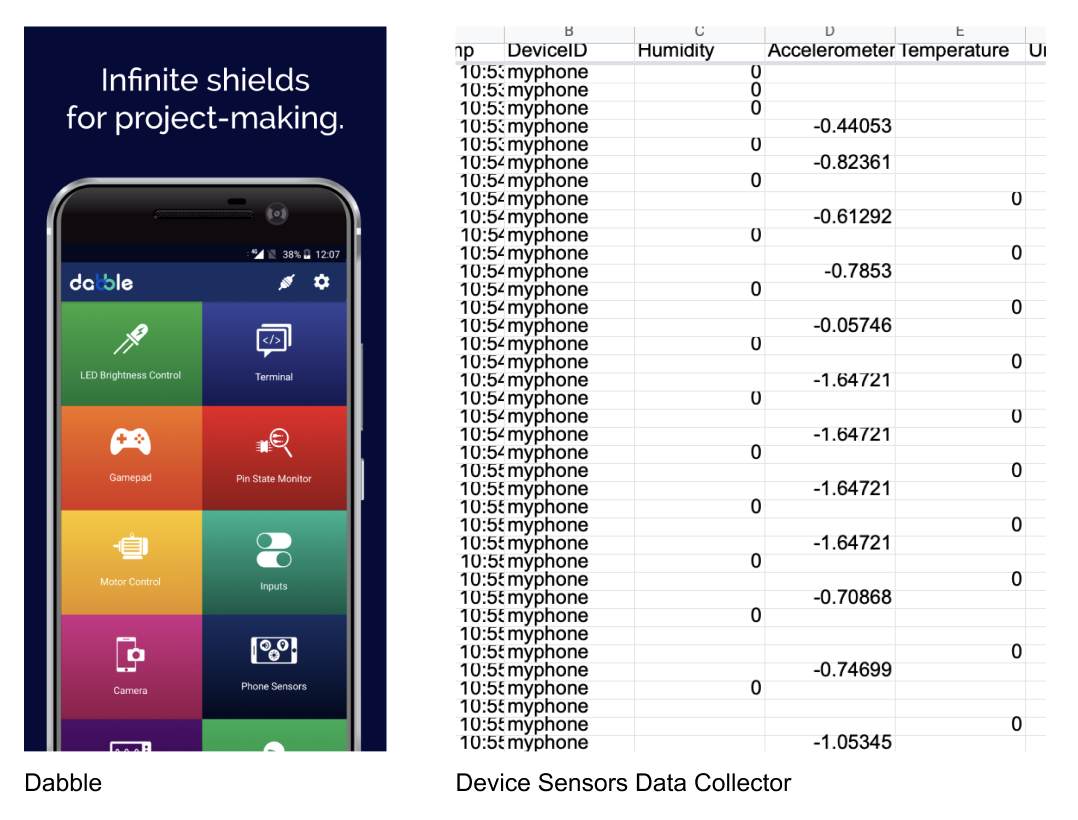
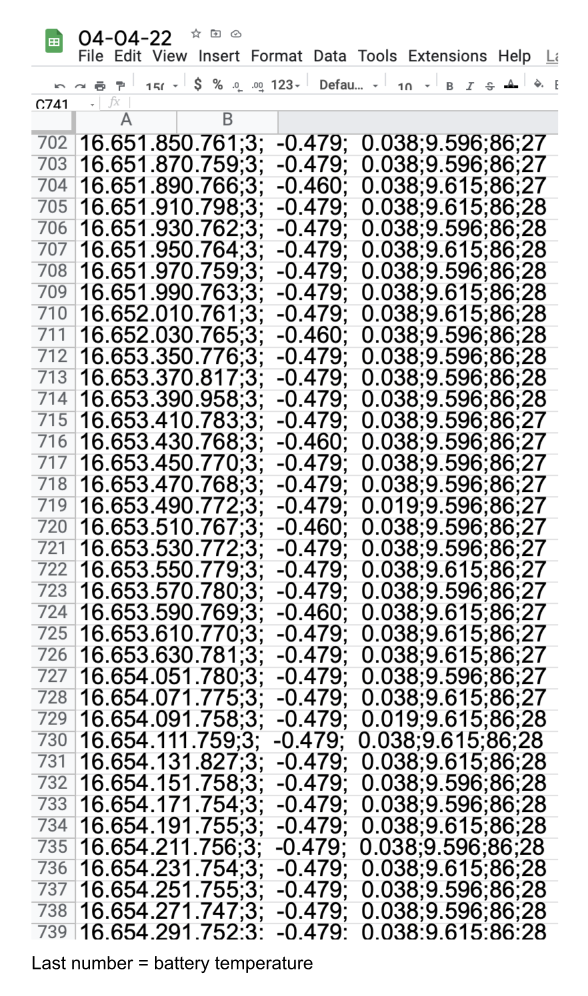
However, this process proved to be rather tricky. Connecting the bluetooth module with the phone was acceptable, but collecting the sensor data was not. Promised applications that specifically work with the Arduino bluetooth module and phone sensors proved to be a bust, resulting in unworkable sensors or non downloadable applications (Sensoduino, Dabble). Looking further, an application was found that was able to send life feed data to a Google spreadsheet, however, temperature data remained 0 (Device Sensors Data Collector). This became a reoccurring problem, as a lot more applications could not provide temperature information. Then when few applications would be able to measure temperature, it could not be shared to Arduino or share live data.
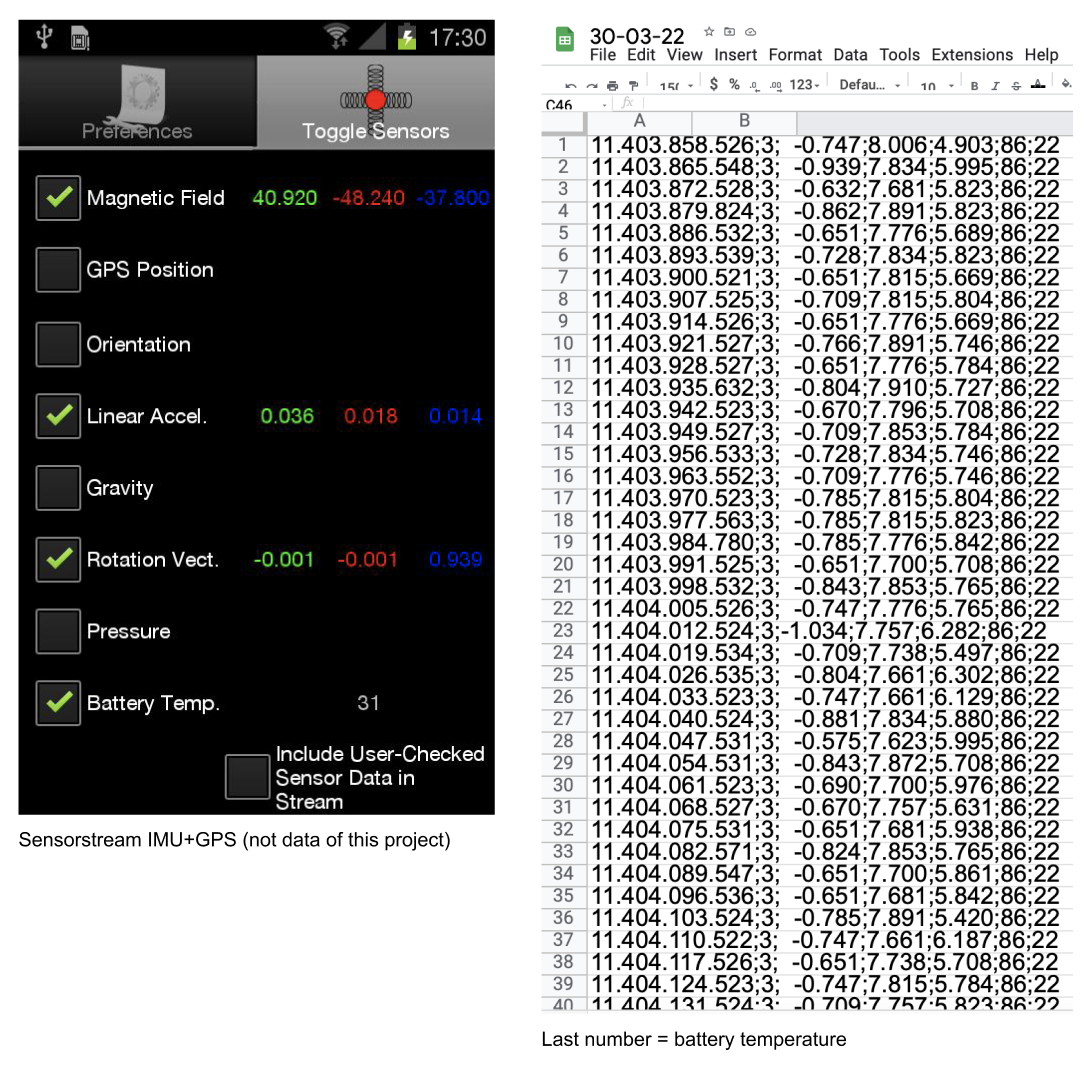
A compromise was found in the application Sensorstream IMU+GPS. This application could read temperature, could give clear data every few seconds, but could not sent it straight through the bluetooth module. Nevertheless, it could send out an .csv file with data, and this .csv file could be send through the bluetooth module.

Insights
- Do not underestimate the technology
ITERATION – 2
The aim of the second iteration was to begin working with the data and to begin testing with some users.
Using

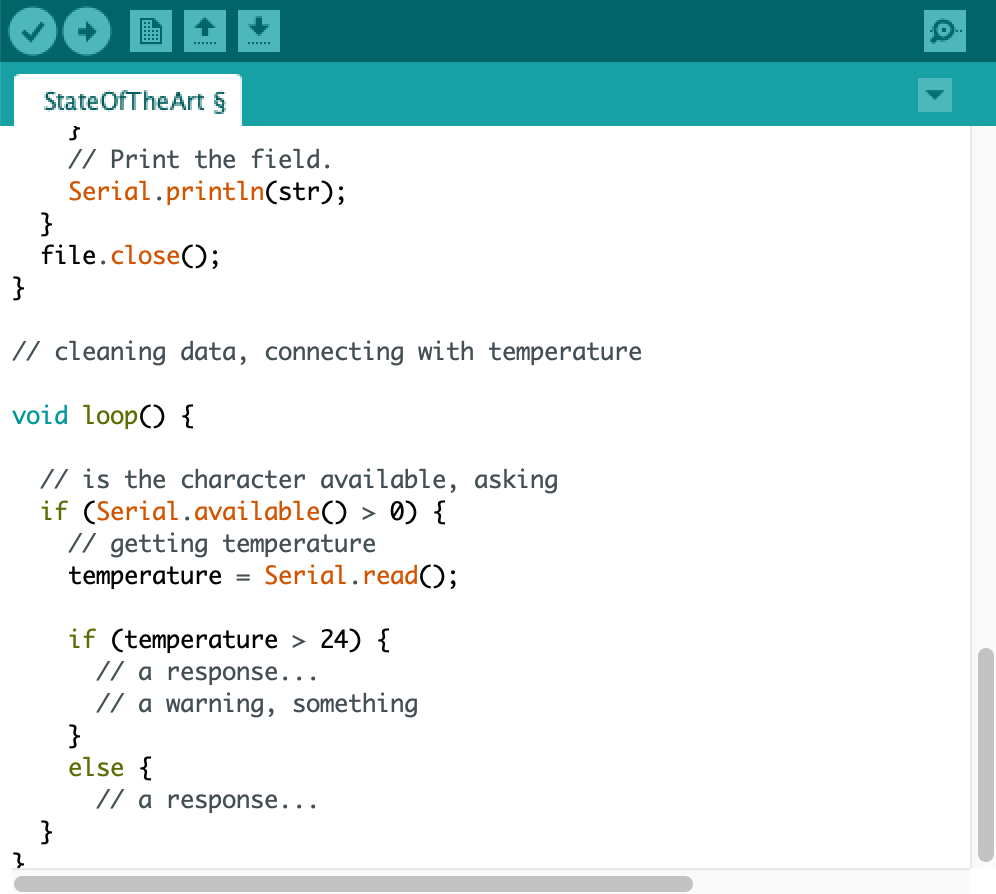
After connecting the data with Arduino, code had to be written. When a temperature would spike up quickly, or if a general high temperature was detected, a special reaction would occur in the code. A normal phone battery temperature lies around 37 to 43 degrees Celsius (Monteclaro, 2019). Nonetheless, when letting the application gather data every few days for a few hours, it always came around 18 to 24 degrees Celsius. This data was being collected while the phone was not charging, had no other programs open, the screen was off and there was a moderate low room temperature, which all perhaps could explain the lower degrees. If the temperature would fall above 24 degrees, then the code would make something happen.
To figure out what exactly would happen, some user testing needed to be done. Small interviews with three people in their twenties gave a tell to how they would prefer to receive information. Conclusions that could be made were for it to be: direct, fun, attention grabbing, subtle visuals, and with some information offering.
Insights
- Old phone gives other data than “normal” phones
- Other factors might play a role in the lower temperatures
- However, important to continue with the same factors, for comparison
- Important to connect to human values
- Users biggest wish: fun notification that grabs attention
ITERATION – 3
The aim of the third iteration was to test if malware can indeed be detected with the use of the temperature sensor, and if the use of fun notification could help users with reacting to it.
Using

The only way to check if malware can be detected is to ingest the old phone with it. Scouting Reddit posts with links, such as https://malwr.com/ and http://www.offensivecomputing.net/, a package was downloaded that was said to contain malware. Repeating the process in iteration 2, multiple days with a few hours of data were collected through the .csv files. Results seem lacking. Overall, the temperature remained the same, however, there is some data that tells that the temperature did go above the 24 degrees Celsius mark, but not by a lot.
To give the user a warning when temperature spikes, a small widget and application concept was born. After collecting the insights from the last iteration, the focus lay on giving subtle but attention grabbing hints. Subtle, looking at the widget format, and fun attention grabbing, which a traffic light could achieve. The colours of a traffic light are also easy to explain, red if temperature is spiking enormously, orange if spikes are timid and green when all is well. The widget would only appear in case of orange or red, like a notification. Furthermore, an application that can give textual information was made to give the user more context to the widget. When telling this concept to two of the interviewed, the feedback was positive and generally liked.

Insights
- Difficult to check if malware was really present on phone.
- Temperature does not seem to have a strong link in detecting malware. Is it because of phone, the inactivity, or the overall sensor?
- Big spikes in data were not seen
- Users values were met
- Traffic light might give wrong impression, more testing is needed
CONCLUSION
More testing is needed. For future research focus should play more into the traffic light idea. As of right now, it was a secondary focus. When iterating more around the look and feel, more human values could be met and the better the prototype could become. Moreover, gathering implementation insights revealed that a lot more can be discovered about malware sensing. This research only tasted the beginning, and more factors than initially thought could influence the data.
In conclusion, the prototype has succeeded in giving an indication to users if possible malware could be active on their phone. Despite a rough start, results do show a slight change when the mobile became corrupted. This gives confidence to the idea that mobile sensors could indeed help with identifying trojan malware, and therefore could help make an impact in fighting cybercrime.
REFERENCES
Resources
Brous, P., Janssen, M., & Herder, P. (2020). The dual effects of the Internet of Things (IoT): A systematic review of the benefits and risks of IoT adoption by organizations. International Journal of Information Management, 51, 101952. https://doi.org/10.1016/j.ijinfomgt.2019.05.008
Chau, N. H. (2019). Estimation of air temperature using smartphones in different contexts. Journal of Information and Telecommunication, 3(4), 494–507. https://doi.org/10.1080/24751839.2019.1634869
Chng, S., Lu, H. Y., Kumar, A., & Yau, D. (2022). Hacker types, motivations and strategies: A comprehensive framework. Computers in Human Behavior Reports, 5, 100167. https://doi.org/10.1016/j.chbr.2022.100167
Gracián, B. (2015). How to Use Your Enemies (12 ed). Penguin.
Houde, S., & Hill, C. (1997). What do Prototypes Prototype? Handbook of Human-Computer Interaction, 367–381. https://doi.org/10.1016/b978-044481862-1.50082-0
Kokolakis, S. (2017). Privacy attitudes and privacy behaviour: A review of current research on the privacy paradox phenomenon. Computers & Security, 64, 122–134. https://doi.org/10.1016/j.cose.2015.07.002
La Porta, L. (2021, 1 oktober). Back to security basics: malware. Jamf. From https://www.jamf.com/blog/youve-got-malware/
Lishchuk, R. (2021, 15 juni). How to Find and Remove Malware on Your Android Device. Clario. From https://clario.co/blog/how-to-remove-malware-from-android/
McClelland, C. (2016, 29 oktober). IoT Explained – How Does an IoT System Actually Work? Leverege. From https://www.leverege.com/blogpost/iot-explained-how-does-an-iot-system-actually-work
Monteclaro, A. J. (2019, 20 april). Why My Phone Gets Hot and How to Cool it Down? MalwareFox. From https://www.malwarefox.com/why-phone-hot/
Monteith, S., Bauer, M., Alda, M., Geddes, J., Whybrow, P. C., & Glenn, T. (2021). Increasing Cybercrime Since the Pandemic: Concerns for Psychiatry. Current Psychiatry Reports, 23(4). https://doi.org/10.1007/s11920-021-01228-w
PurpleSec. (2021, 6 augustus). 2021 Cyber Security Statistics: The Ultimate List Of Stats, Data & Trends. From https://purplesec.us/resources/cyber-security-statistics/
Tillu, J. (2021, 7 december). Mobile sensors: The Components that make our smartphones smarter. Medium. From https://medium.com/jay-tillu/mobile-sensors-the-components-that-make-our-smartphones-smarter-4174a7a2bfc3
Valeo Networks. (2021, 10 september). How Is the Internet of Things (IoT) Being Impacted by Malware? From https://www.valeonetworks.com/how-is-the-internet-of-things-iot-being-impacted-by-malware/
Zarkov, G. (2020, 17 januari). Can a smartphone measure temperature like a thermometer? Phone Arena. From https://www.phonearena.com/news/can-smartphone-take-temperature_id121600
Images
A., & A. (z.d.). iPhone Download gratis PNG | PNG Play. PNG Play. From https://www.pngplay.com/nl/image/473034
Android-apps op Google Play. (z.d.). Google Play. From https://play.google.com/store/apps?hl=nl&gl=US
Belcic, I. (2021, 19 november). What is a Trojan Malware? The Ultimate Guide. From https://www.avast.com/c-trojan
Girish, M. (2016, 23 mei). Arduino Bluetooth Basic Tutorial. Arduino Project Hub. From https://create.arduino.cc/projecthub/mayooghgirish/arduino-bluetooth-basic-tutorial-d8b737