Premise
Using informative IoT devices and gamification mechanisms to influence privacy behavior.
Synopsis
Research suggests that many people are aware of online privacy problems. However, this awareness does not seem to translate into action. People for example still choose to use privacy-unfriendly services and oftentimes provide more data than necessary. This discrepancy is described as the privacy paradox. The following project explores if the privacy paradox can in part be mitigated by making privacy violations more tangible through IoT devices and gamification mechanisms. A physical prototype was developed that actively alarms users of privacy violations and subsequently provides privacy prevention suggestions that try to trigger users to protect their privacy.
Background
The modern privacy problem is encapsulated by events such as the Cambridge Analytica scandal. When this scheme of mass personal information violation was revealed, outrage ensued only to discover that this misuse of data was quickly forgotten and people returned to the same platforms that were responsible for violating their privacy (Acquisti et al., 2020). This phenomenon is described in literature as the privacy paradox and outlines the discrepancy between an individual’s expressed concern about privacy and their actual behavior (Bath & de Jong, 2017). Researchers have tried to unravel the paradox through behavioral economic theories such as the immediate gratification bias which states that people prefer immediate rewards over future privacy risks and therefore still use privacy-unfriendly services, or by focusing on the potential asymmetric information about consequences and risks of privacy violations (Bandara et al., 2017; Acquisti et al., 2015). Nevertheless, these theories do not seem to have led to practical solutions. Privacy breaches proceed to go largely unnoticed, and people still willingly sacrifice privacy just to use new technologies (Emami-Naeini et al., 2021).
Project
Services like “Haveibeenpwned” collect information about known data breaches and publish this online for users to identify whether their identity has been leaked. Research based on “Haveibeenpwned” data suggests that 83% of Americans have had their identity breached at least once (Cor & Sood, 2018). Unfortunately, many people are not aware of these services, mistake warning emails for spam, and use multiple email addresses making a direct line of communication difficult (Malderle et al., 2018). Meanwhile, the internet of things (IoT) describes the many uses and processes that result from giving a device access to a network. When we equip these devices with a network, they gain the ability to provide new forms of communication with new interfaces (Bunz & Meikle, 2017). This research, therefore, tries to find out if IoT devices can help mitigate the privacy paradox by influencing behavior through new active information communication channels and gamification mechanisms. The first prototype consists of a small device powered by an ESP8266 that will notify users with audio-visual cues in case of a privacy violation in the form of their email address being leaked. This ‘privacy alarm’ tries to bridge the digital world with a tangible device that alarms you.
Iteration 1 – Measuring the initial response
The goal of this iteration was to measure the initial response to an IoT privacy protection device. 4 participants were informed of what the warning meant and then given the device for a day. They were asked to write down how they felt when the device lit up, what they were doing when this happened, and what their initial response would be. At this time, it was not connected to an actual data leak API, because there would have been a high chance that the device wouldn’t be triggered at all. Therefore, the device was triggered externally using MQTT. The alarm triggered at various times for different users since research indicates that notification responses differ based on time and activeness of the user (Saikia et al., 2017)
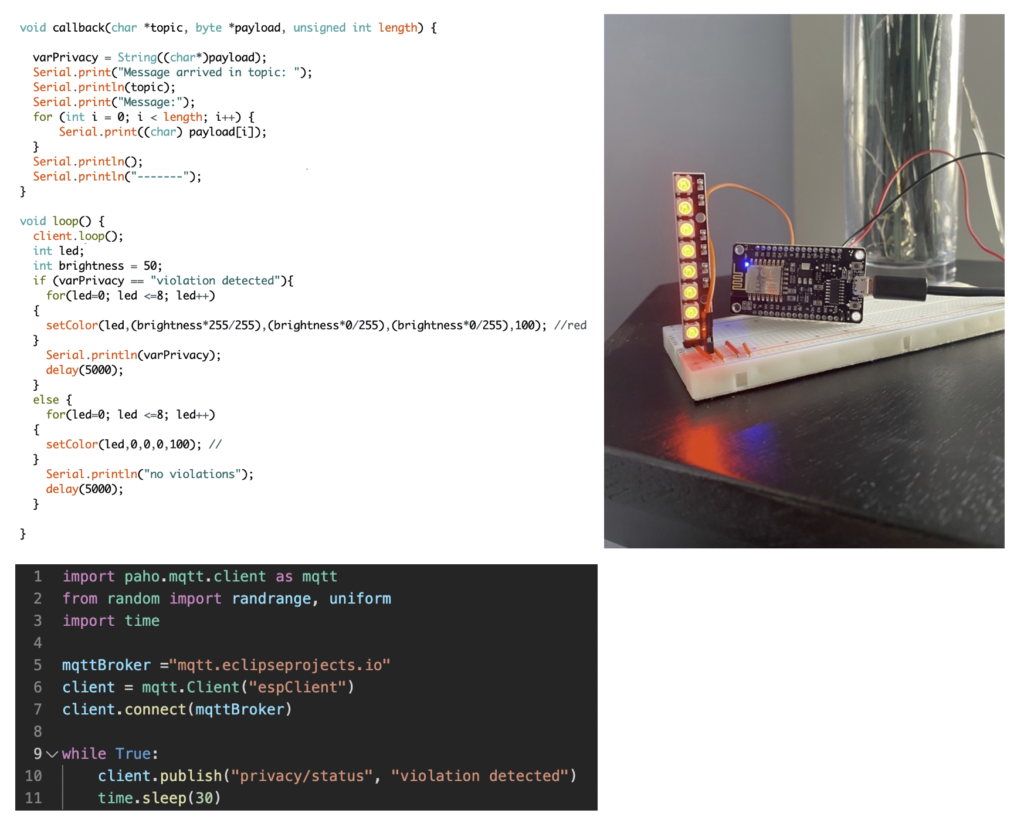
Users that were in the same vicinity and actively looking in the direction of the device when it lit up commented that their first response was being surprised and scared. However, this quickly turned into curiosity about what the warning meant and what they had to do. Users also commented that they didn’t find it useful to have a device in their house that nine out of ten times did not do anything. They found it more useful if they could also interact with it in other ways when there was no data breach incident. One user specifically mentioned that it would be nice if they could play with it. Therefore, the main insights gained from user testing were that the device would need to inform better, should also display something when there is no data breach, and allow for more ways of interaction such as through gamification.
Iteration 2 – Inform users & add gamification mechanisms
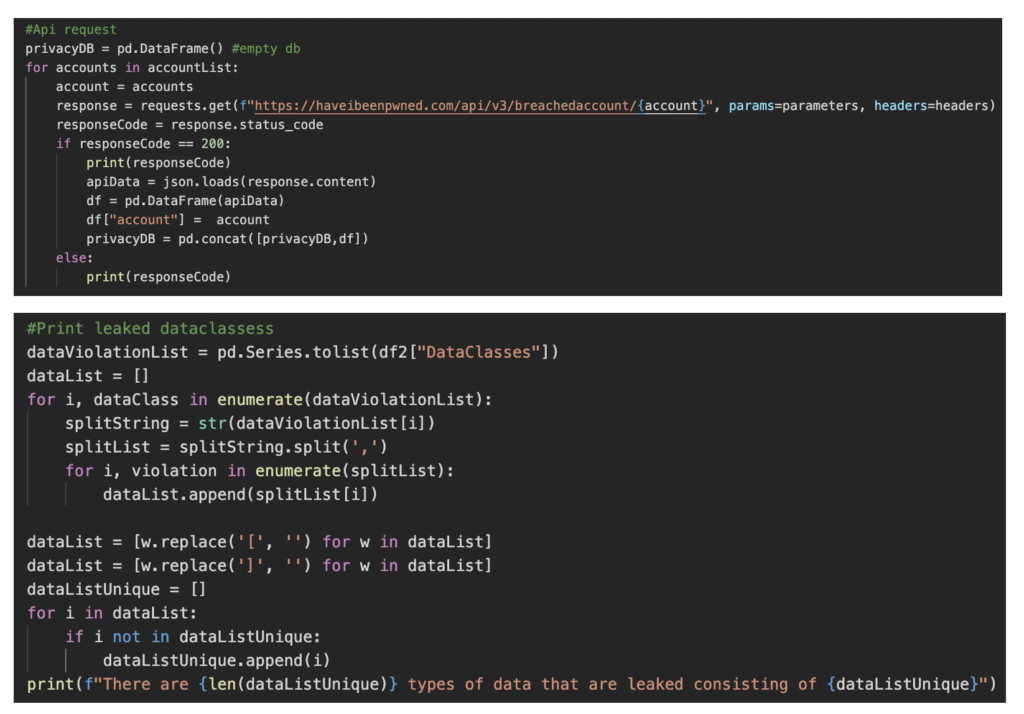
This iteration added a display to inform the users better. The screen shows the number of leaks, number of leaked data classes such as phone number or IP address, information about the latest leak, and privacy advice. The data leak information is automatically gathered from the “haveibeenpwned” API and published to the device via MQTT.
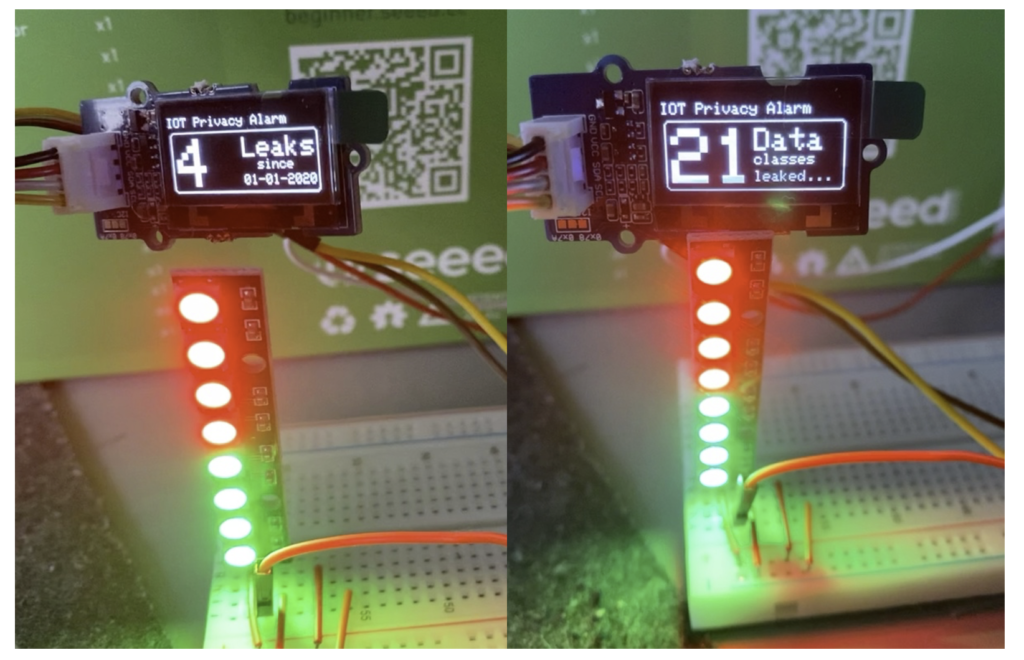
Furthermore, when there is no leak detected, the LED lights indicate the number of ‘lives left’ as a gamification mechanism. Gamification is the use of game elements in non-game contexts. These game elements can create a more entertaining and appealing environment that allows for increased interaction (Mavroeidi et al., 2020). Every time a life is lost due to a newly detected leak, another LED will turn red. The goal is to keep all your lights green thereby achieving a satisfactory healthy privacy status. Unfortunately, it is not always possible to prevent your data from leaking which results in losing lives. Therefore, the display also notifies users of privacy preventing actions that help protect themselves from future intrusions. Examples are using VPNs, deleting cookies at a regular interval, and using privacy-friendly search engines. The user can regain lives if they accomplish actions and notify the device by pushing a button. It can be played individually, but also with your household members. This allows for social interaction because you work together to maintain your privacy levels. In essence, the game is a backdrop for discussing privacy measures and motivating each other to act.
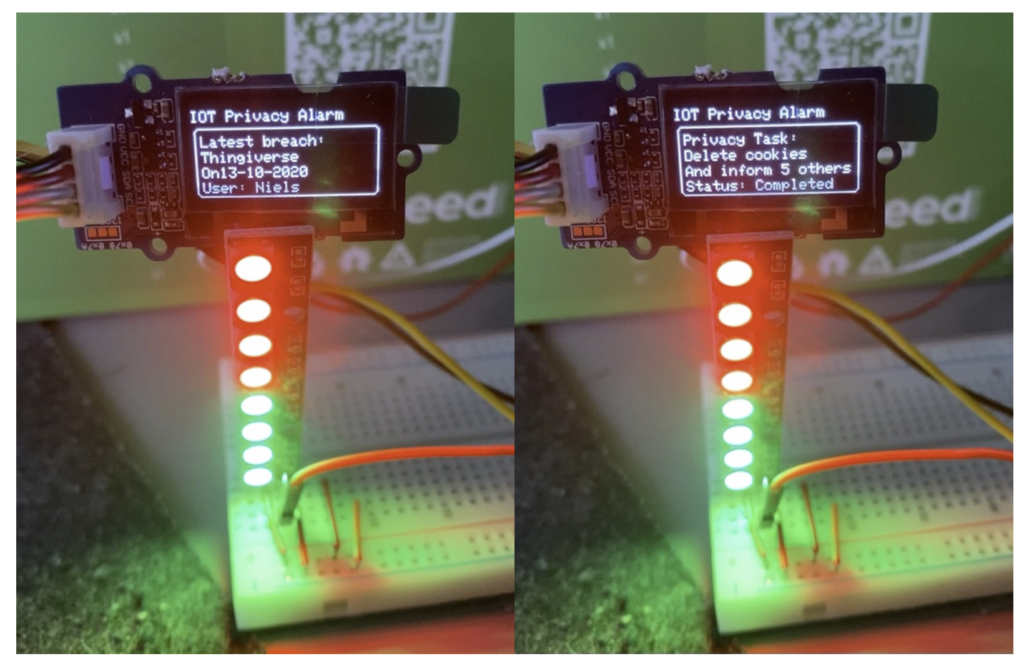
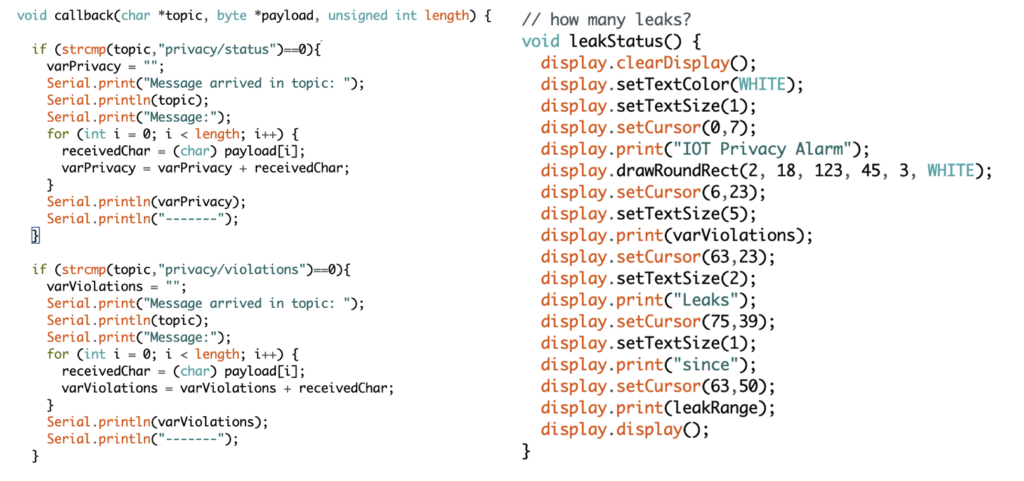
This iteration was individually tested with four participants. First, the goal of the device and the game mechanics were explained. The users then entered their e-mail address to display personal leak information on the device after which the game mechanics were manually triggered and discussed in short 20-minute sessions. The participants thought it was an interesting device that grabs your attention and could be a conversation starter. However, the replay value was questioned since at some point you have taken most privacy preventing actions. Nevertheless, the participants admitted that by reaching this point, the goal of the device is already achieved. Another insight was that the warning light should be turned off manually. This increases interaction with the device, but more importantly, makes sure that you’ve seen the warning. Finally, they mentioned that increasingly advanced scoring mechanisms make the game more interesting. Perhaps turning off the alarm quicker and taking privacy preventing action would not only return lives but also result in points.
Iteration 3 – Continuous improvement
The final version implemented several improvements. The warning message now needs to be turned off manually, a simple scoring mechanism was added for completing privacy preventing actions, and everything was put together in a case since it seemed that several users had difficulties looking beyond the breadboard setup and mentioned that the appearance of the device is important to them. Two participants tested the device a day and night.

The main insights during this test were that users would like to be informed of more privacy violations to increase usefulness. Feasible options included leaked passwords and network intrusions. Furthermore, they would like the device to also have an audio alarm, although they didn’t know if it would annoy them in the long term since they thought the current light solution was perhaps more friendly. Unfortunately, this couldn’t be tested due to a malfunctioning buzzer and time limitations. The final remark was that they would like to be able to compare their scores with others.

Conclusion
Participants stated that the IoT device was able to raise awareness by combining abstract privacy violations with a physical device they could interact with. This increased their likelihood of taking privacy preventing actions because although they cared about their privacy, it was not part of their daily routine. Therefore, IoT devices create interesting opportunities for new ways of interaction that could positively influence people. Nevertheless, all participants found privacy important to begin with, which raises questions about its effectiveness for people that not yet have privacy on their mind. This means the device should be tested with more people during longer periods of time to make definitive conclusions about its effectiveness. Furthermore, the gamification mechanisms need to be more advanced and tested with different types of users (Bartle, 1996). Finally, future iterations could also benefit from the inclusion of additional privacy threats and leaderboards.
Literature
Acquisti, A., Brandimarte, L., & Loewenstein, G. (2015). Privacy and human behavior in the age of information. Science, 347(6221), 509–514. https://doi.org/10.1126/science.aaa1465
Acquisti, A., Brandimarte, L., & Loewenstein, G. (2020). Secrets and Likes: The Drive for Privacy and the Difficulty of Achieving It in the Digital Age. Journal of Consumer Psychology, 30(4), 736–758. https://doi.org/10.1002/jcpy.1191
Bandara, R., Fernando, M., & Akter, S. (2017). The Privacy Paradox in the Data-Driven Marketplace: The Role of Knowledge Deficiency and Psychological Distance. Procedia Computer Science, 121, 562–567. https://doi.org/10.1016/j.procs.2017.11.074
Barth, S., & de Jong, M. D. T. (2017). The privacy paradox – Investigating discrepancies between expressed privacy concerns and actual online behavior – A systematic literature review. Telematics and Informatics, 34(7), 1038–1058. https://doi.org/10.1016/j.tele.2017.04.013
Bartle, R. (1996). Hearts, clubs, diamonds, spades: Players who suit MUDs. Journal of MUD research, 1(1), 19.
Bunz, M., & Meikle, G. (2017). The Internet of things. Polity.
Cor, K., & Sood, G. (2018). Pwned: How Often Are Americans’ Online Accounts Breached? https://doi.org/10.48550/ARXIV.1808.01883
Emami-Naeini, P., Dheenadhayalan, J., Agarwal, Y., & Cranor, L. F. (2021). Which Privacy and Security Attributes Most Impact Consumers’ Risk Perception and Willingness to Purchase IoT Devices? 2021 IEEE Symposium on Security and Privacy (SP), 519–536. https://doi.org/10.1109/SP40001.2021.00112
Malderle, T., Wübbeling, M., Knauer, S., Sykosch, A., & Meier, M. (2018). Gathering and Analyzing Identity Leaks for a Proactive Warning of Affected Users. Proceedings of the 15th ACM International Conference on Computing Frontiers, 208–211. https://doi.org/10.1145/3203217.3203269
Mavroeidi, A.-G., Kitsiou, A., & Kalloniatis, C. (2020). The Role of Gamification in Privacy Protection and User Engagement. In C. Kalloniatis & C. Travieso-Gonzalez (Red.), Security and Privacy From a Legal, Ethical, and Technical Perspective. IntechOpen. https://doi.org/10.5772/intechopen.91159
Saikia, P., Cheung, M., She, J., & Park, S. (2017). Effectiveness of Mobile Notification Delivery. 2017 18th IEEE International Conference on Mobile Data Management (MDM), 21–29. https://doi.org/10.1109/MDM.2017.14