Sophie van Dael 1713547 State of the Art
Premise
Exploring and explaining the functionality of smart contracts in the protection of explicit photos shared through sexting among 18 – 35-years-olds.
Synopsis
As all aspects of modern human life evolve to include online components, it is only common sense that dating transformed as well. As dating shifts to an online environment, new risks arise. A huge risk affecting those who experience (part of) their relationships online, has been the ease with which explicit photographs can be shared to others. This practice is commonly known as ‘revenge porn’. This occurs when a partner shares intimate photos send to them in private to others. To shift the conversation and provide users with a proactive stance towards this issue rather than a restrictive one, I will be researching the functionalities of smart contracts and to what extent they can aid in combatting this issue.
Revenge porn
Revenge porn can be defined as the distribution of sexually explicit photographs to third parties with the intent to harm, or gain control of the victim (Harper et al, 2021). Over the past few years, countries have undertaken steps to set-up a legal framework to address this offense, but actionable solutions to prevent the crime from happening have yet to be proposed (Ruvalcaba, 2021). Instead, most solutions are aimed at restricting the sender, and often protect the perpetrator through a sense of invisibility (Scott et al., 2018).
Although sending explicit photos bears consequences, it does not stop people from sending explicit pictures to their partner: research reports about a third to one half of adults between the ages of 18 to 26 engage in this behavior (Benotsch et al., 2012). This is most commonly done through online acquaintance based environments (ABE), where users have relationship together (Jorgensen & Demant, 2021). As this form of intimacy displayed by new generations is obviously desired, safer alternatives to this should be explored where protection of the sender takes center stage.
Smart contracts
Smart contracts are an important beneficial component of blockchain technology. They are self-executing contracts, in which the terms and conditions are set using software codes (Buterin et al., 2014). The contracts cannot be forged, and data protection is at the center of this technology, they also allow for vigilant identification of users and the right to revoke access to certain data (Zhang et al., 2021).
After initial research into the technical side of smart contacts, the best way to explore and create an entry-level smart contract seems to be the program language Solidity. Solidity is a new language launched to function on the Ethereum blockchain. It bears similarities to languages such as Python, and functioned as a good starting point for me to discover the technical side of smart contracts. As participants were not knowledgeable about programming, I translated the functions of the smart contract in my prototype to a visual design, for users could not provide insight into programming.
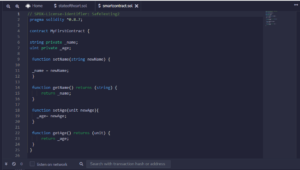
Simple smart contract in solidity; protecting data variables.
Prototyping
To research if the introduction of a smart contract into the online exchange of explicit photos is meaningful to users, I asked 4 people who have previously shared explicit photos to be the test audience for my iteration rounds.
Iteration
Iteration 1
Prototype
As none of the participants had any experience with smart contracts, my first iteration focused on explaining the workings in the context of this problem. To ensure the understanding of the participants, I created a low-fidelity prototype through paper and attributes, such as keys, a paper contract, and a Tupperware.

- First iteration round
Testing
I tested the prototype per duo, and asked them through role-play to imagine being in the scenario of sending a photograph. I used Tupperware to resemble the safe locking of data on the blockchain. Both were given keys, which with they could access the photograph. Through storytelling, I explained the main functions the smart contracts introduces (the security layer, individual ‘keys’, and the right to revoke access by one of the partners).
Results
The very simplistic prototype ensured the participants would not be overwhelmed while clearly explaining the attributes of smart contracts. The storytelling element was essential, as it conveyed to the participants an understanding of the severity of being a victim to this crime, and the lack of self-protection. Benefits of the prototype included the right to revoke access, although the participants were unclear how this would work into real-life online situations.
Insights
- The risk of sending explicit photos is noted but not feared to a level that results in abstaining.
Solutions focused on restriction are futile.
- The trust for the partner, combined with a sense of duty, trumps the potential consequences.
The solution needs to be easily integrated into their habits, too much effort will result in non-use.
- A proactive need for a way to protect the sender is necessary, as the trust alone is not enough long-term.
Protection of the senders should be prioritized.
Iteration 2
Prototype
The main question left unanswered by the participants was how the smart contract would function in real life. To display this, I created a paper prototype displaying the attributes of the smart contract. These are:
- Both parties can only access the photo with a mutual ‘key’, which they can use.
- When the relationship has ended, one can revoke access.

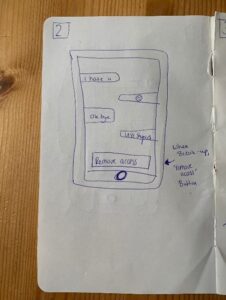
2. Attributes of the smart contract, paper prototype
Testing
The second testing phase focused on the selection of the parameters and attributes of the smart contract. Through co-creation, participants were encouraged to critique and add to said smart contract. To implement the smart contract into their daily lives, the prototype showed a texting environment similar to WhatsApp.

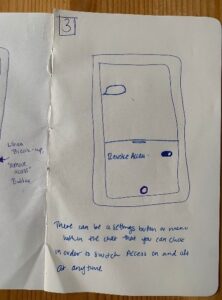
- Co-creation, suggestion of alternated attribute by participant.
Results
All participants valued the prototype being integrated into a familiar environment. Getting an access ‘key’ to see the photograph stimulated a sense of safety and was important to all participants. One participant remarked the importance of not limiting revoked access to only the end of the relationship, but rather be an option to the sender at all times (in event of a fight, cheating etc.)
Insights
- The right to revoke access to shared photos should be more flexible, the sender should be able to set the parameters.
Access should be broadened so access to photos can be revoked at any given moment.
- The participants value the smart contract and its attributes, but they are not likely to seek this out alone.
The smart contract should be employed within a familiar environment.
- Participants suggested the ‘no screenshot’ function of Netflix as extra protection.
Photos cannot be screenshotted.
Iteration 3
Prototype


4. Attribute of online prototype; the red button allows the sender to restrict access.
To implement the changes into a visual, online design, all feedback was realized into an updated online prototype in Figma, that displays the working of the smart contract.
Testing
Participants were asked to interact with the prototype online and judge the overall concept according to a user-experience questionnaire.
Results
The participants appreciated the implementation of the smart contract into their familiar surroundings. They acknowledged the change in perspective it brought into the consequences of sending explicit photos and the lack of self-protection currently available. They were pleased with all implemented features.
Insights
- It is important for participants to be able to retract consent to photos at any given time.
A key value of the final prototype is the autonomy of the sender.
- The prototype shifts the perspective of participants to better protect themselves from their partners distributing their photos without consent.
The prototype offers insightful information to the possibility of protecting the sender which is currently not provided by traditional online channels, such as WhatsApp.
Further research
For future perspectives, it would be beneficial to investigate the technical possibilities and challenges of creating a plug-in smart contract, and if the Ethereum network is a mere option, or if there are other ways of pursuing this (possibly even outside of blockchain).
References
Benotsch E., Snipes D., Martin A., Bull S. (2013). Sexting, substance use, and sexual risk behavior in young adults. J. Adolesc. Health 52, 307–313.
Harper, C., Fido, D., and Petronzi, D. (2021). Delineating non-consensual sexual image offending: Towards an empirical approach. Retrieved from; https://www.sciencedirect.com/science/article/pii/S135917892100001X
Jørgensen, K. E., & Demant, J. (2021). Shame, shaming and economy: A theory of image-based sexual abuse within different online sharing environments. First Monday, 26(4). https://doi.org/10.5210/fm.v26i4.11670
Ruvalcaba, Y., & Eaton, A. A. (2020). Nonconsensual pornography among U.S. adults: A sexual scripts framework on victimization, perpetration, and health correlates for women and men. Psychology of Violence, 10(1), 68–78. Retrieved from; https://doi.org/10.1037/vio0000233
Scott, G., Brodie, Z., Wilson, et al. (2020) Celebrity abuse on Twitter: The impact of tweet valence, volume of abuse, and dark triad personality factors on victim blaming and perceptions of severity. Retrieved from; https://www.sciencedirect.com/science/article/pii/S0747563219303462?casa_token=pebeQGm_miwAAAAA:SxmupLgJCREi3e_eYmMIaOS4NR8uN5Hn-RXQtU8j5EeudV7vro8ywSfqTSxXIJ02QZqyKi4wxvEB#bib40
Zhang et al., (2021). Secure and Efficient Data Storage and Sharing Scheme Based on Double Blockchain. Retrieved from; https://scholarworks.bwise.kr/sch/handle/2021.sw.sch/2215
Read more "Safe sexting; the functionality of smart contracts within sharing explicit photos"